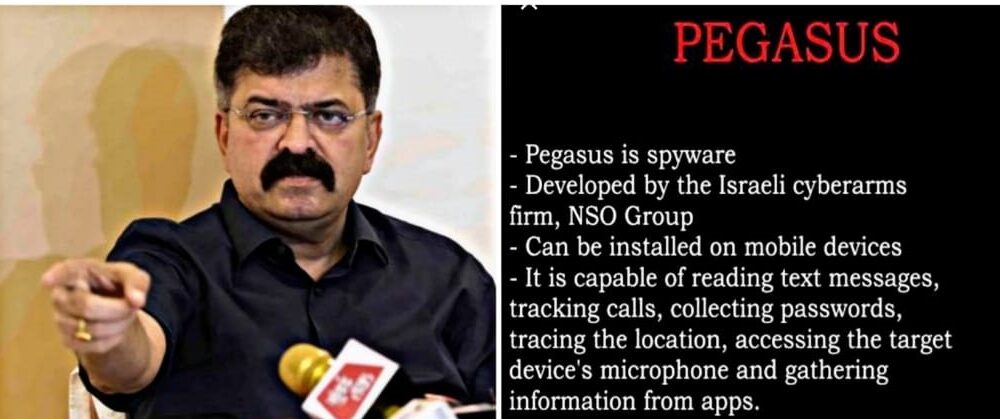
NCP Leader Dr Jitendra Awhad said, “According to Pegasus, they do not sell their software to anyone. They are sold only to the recognized government of the country concerned. However, they are not ready to name the 40 countries that have taken it.
Dr Awhad added, “According to experts Pegasus costs $ 10 million to tap/hack 50 phones. Imagine total cost when such large number of phones were surveilled. This is taxpayers money. Who sanctioned it? Is there another scam lurking behind?”
Dr Awhad added “The malware #pegasus cannot be purchased and used by anybody it is given to #Government on their official purchase order the malware is manufactured in #Israel by #cidrium”
The full response by the Ministry of Electronics and Information Technology
India is a robust democracy that is committed to ensuring the right to privacy to all its citizens as a fundamental right. In furtherance of this commitment, it has also introduced the Personal Data Protection Bill, 2019 and the Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021, to protect the personal data of individuals and to empower users of social media platforms.
The commitment to free speech as a fundamental right is the cornerstone of India’s democratic system. We have always strived to attain an informed citizenry with an emphasis on a culture of open dialogue.
However, the questionnaire sent to the Government of India indicates that the story being crafted is one that is not only bereft of facts but also founded in pre-conceived conclusions. It seems you are trying to play the role of an investigator, prosecutor as well as jury.
Considering the fact that answers to the queries posed have already been in public domain for a long time, it also indicates poorly conducted research and lack of due diligence by the esteemed media organisations involved.
Government of India’s response to a Right to Information application about the use of Pegasus has been prominently reported by media and is in itself sufficient to counter any malicious claims about the alleged association between the Government of India and Pegasus.
India’s Minister of Electronics & IT has also spoken in detail, including in the Parliament, that there has been no unauthorised interception by Government agencies. It is important to note that Government agencies have a well established protocol for interception, which includes sanction and supervision from highly ranked officials in central & state governments, for clear stated reasons only in national interest.
The allegations regarding government surveillance on specific people has no concrete basis or truth associated with it whatsoever.
In the past, similar claims were made regarding the use of Pegasus on WhatsApp by Indian State. Those reports also had no factual basis and were categorically denied by all parties, including WhatsApp in the Indian Supreme Court.
This news report, thus, also appears to be a similar fishing expedition, based on conjectures and exaggerations to malign the Indian democracy and its institutions.
In India there is a well established procedure through which lawful interception of electronic communication is carried out in order for the purpose of national security, particularly on the occurrence of any public emergency or in the interest of public safety, by agencies at the Centre and States. The requests for these lawful interception of electronic communication are made as per relevant rules under the provisions of section 5(2) of Indian Telegraph Act ,1885 and section 69 of the Information Technology (Amendment) Act, 2000.
There is an established oversight mechanism in the form of a review committee headed by the Union Cabinet Secretary. In case of state governments, such cases are reviewed by a committee headed by the Chief Secretary concerned.
The procedure therefore ensures that any interception, monitoring or decryption of any information through any computer resource is done as per due process of law.